A couple of days ago, we noticed that a few somewhat suspicious text messages, claiming to give the user "free internet" and other things, was being circulated. The download link in the SMS, along with others received, claiming "To find any Bangladeshi number location and number owner address information, please just visit the following link:" and "Free Antivirus Download", were sent to the Beetles Threat hunting team for analysis of a suspected malware attack.
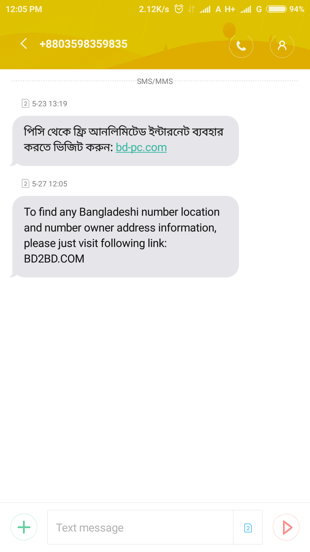
Beetles’ Advanced Persistent Threat (APT) Hunting Team, quickly identified, from the links in the sms, that once a user visits the threat actor's domains and clicks on submit, the following took place:
- www.bd2bd.com and www.registerbd.com - Downloads a weaponised .doc file.
- www.pc-net.org - downloads a Compressed ZIP folder containing 3 weaponised .doc files.
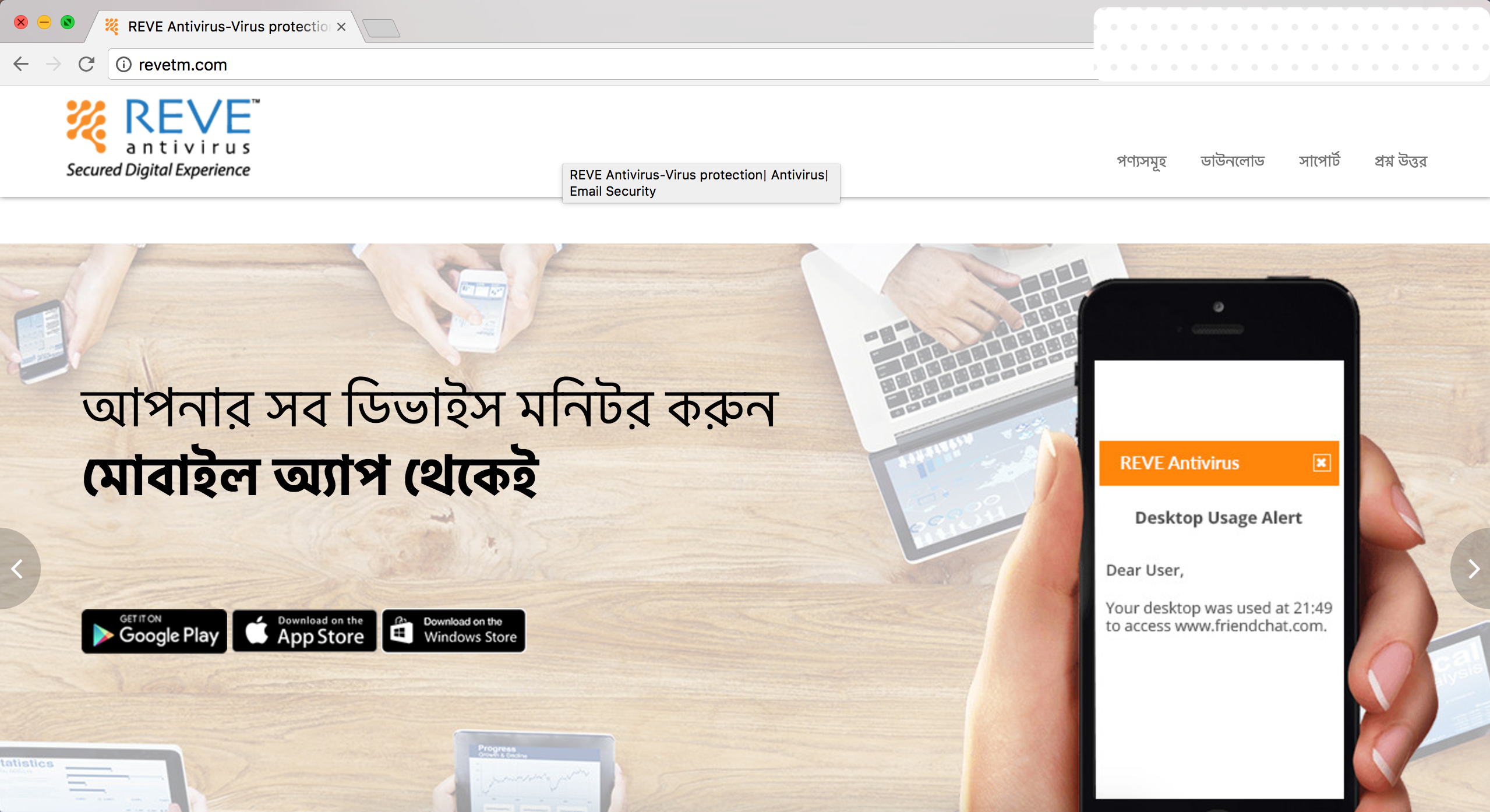
- www.revetm.com - downloads a .exe file.
The purpose of the .doc files are to serve as a malware delivery mechanism to infect the user PC with a Remote Access Tool (RAT). To be specific, the threat actor is using the Luminosity malware family Link's RAT, which can be found online and costs as little as $39.99 for a lifetime license. The RAT is a trojan software that works in the background and allows a remote "operator" to control a system as if they have physical access to that system. Even though there are multiple desktop sharing and remote administration readily available in the market, a RAT is installed as a trojan and runs without the victim's knowledge. It has a malicious intent and is able to hide its processes from the victim as well as most antivirus softwares.
The Operation, labeled "Operation Brightroar", yielded that the threat actor was infecting unsuspecting users with his version of the Luminosity Remote Access Tool and is able to conduct detailed surveillance on the user's device, including logging all keystrokes, extracting passwords from major web browsers and email clients and search for and upload specific files from the user's device, among other things.
Recon of the Phishing sites
We received multiple campaign SMS of the following websites:
- Bd2bd.com
- Pc-net.org
- Bd-pc.com
- Registerbd.com
- Revetm.com
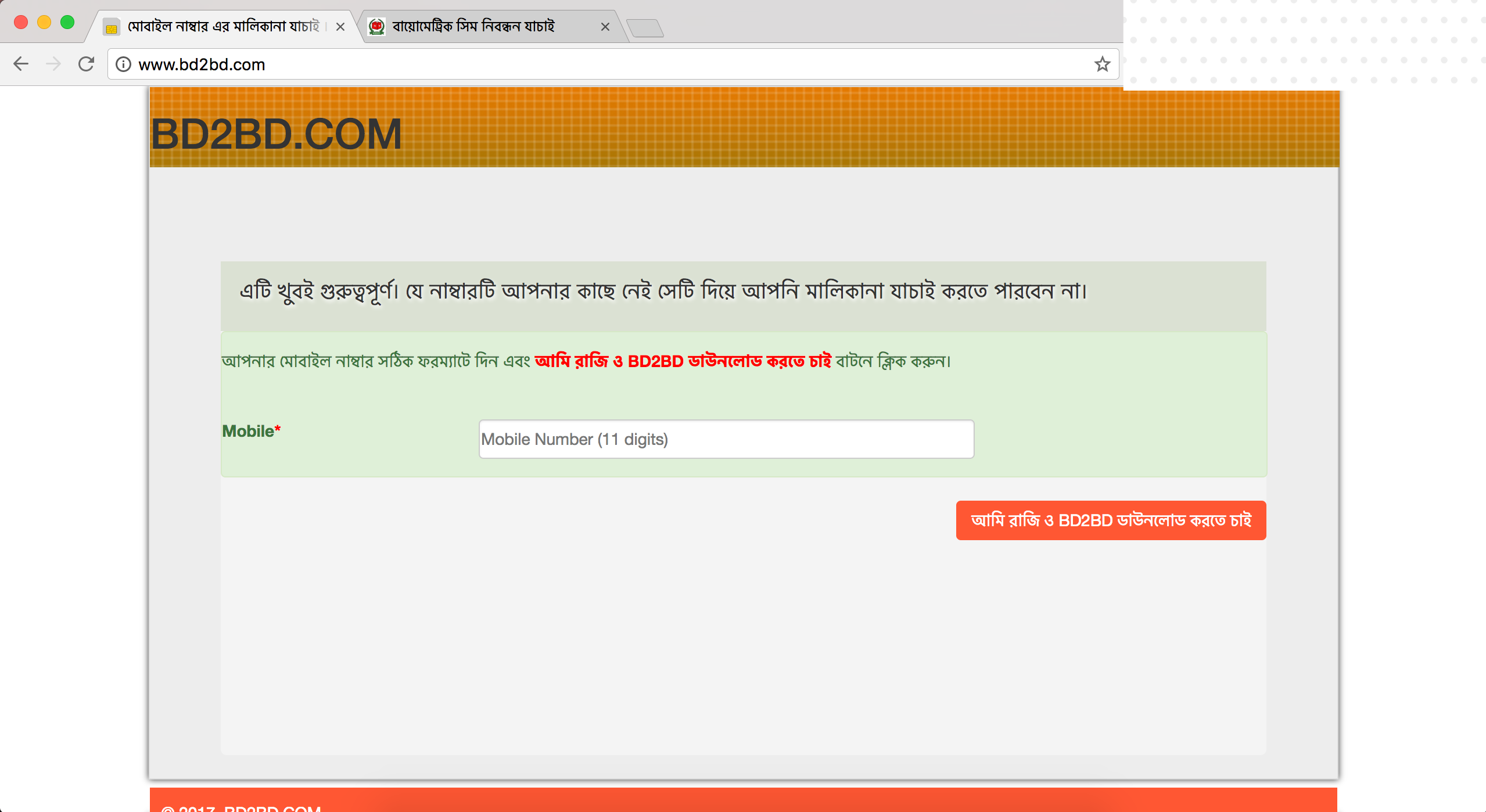
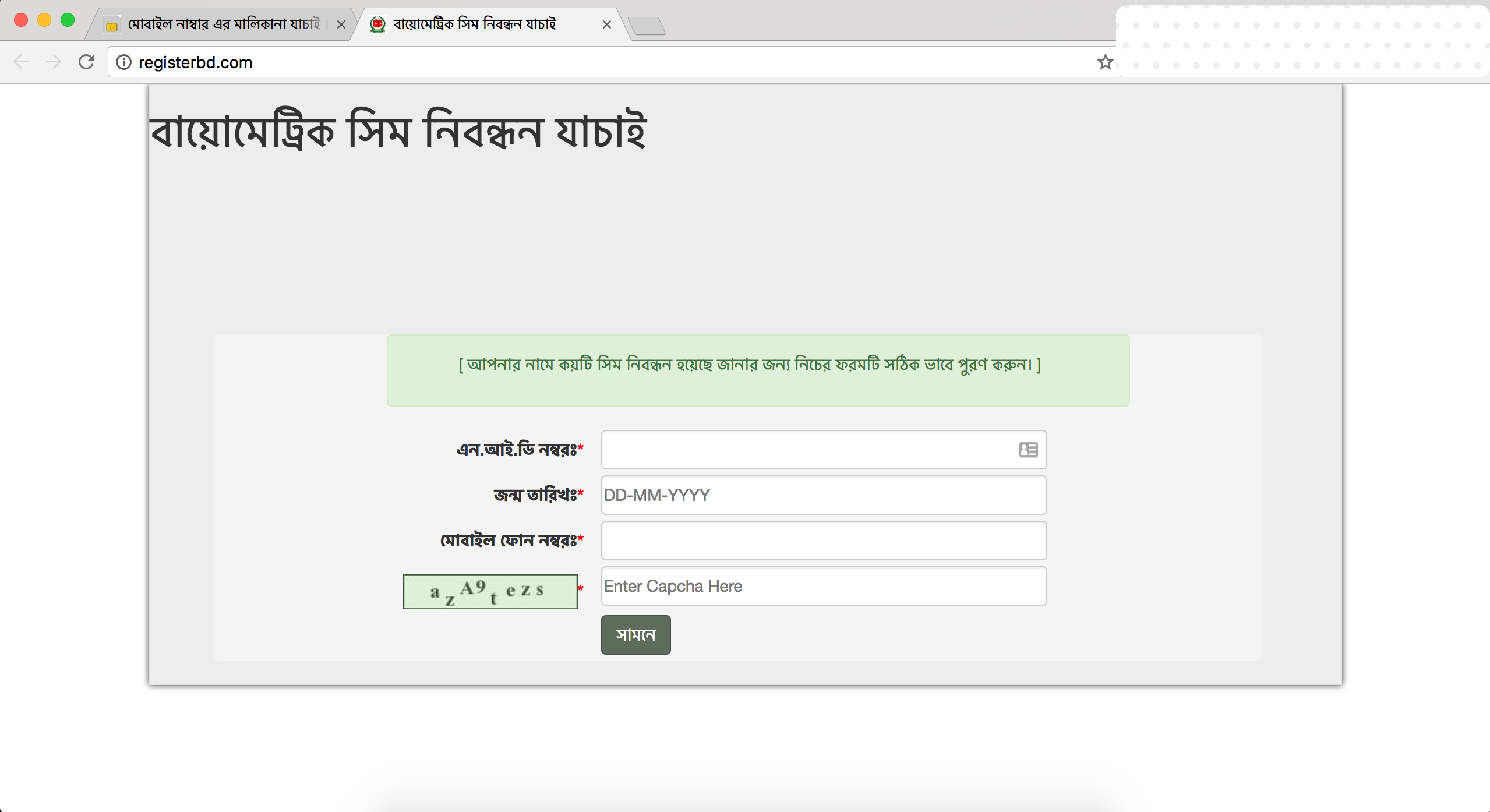
The first 4 websites were found to be hosted on the same web server. But the last website, which uses a clone portal for Reve antivirus as a decoy was hosted on a separate web server.
The Exploit
The document files, which were downloaded from those phishing websites were suited with the following exploits:
Behaviour Analysis
The downloaded document file had no content and the office suite crashes as soon as any user opens them. The crashing was an indication of successful exploitation.
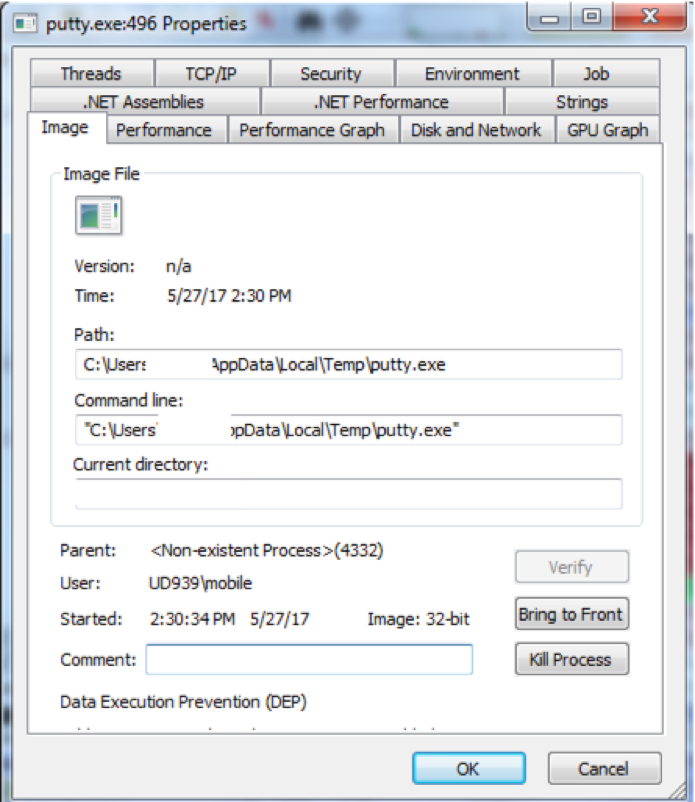
 The malware drops a file, putty.exe and executes it.
The malware drops a file, putty.exe and executes it.
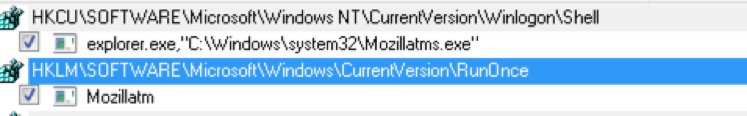
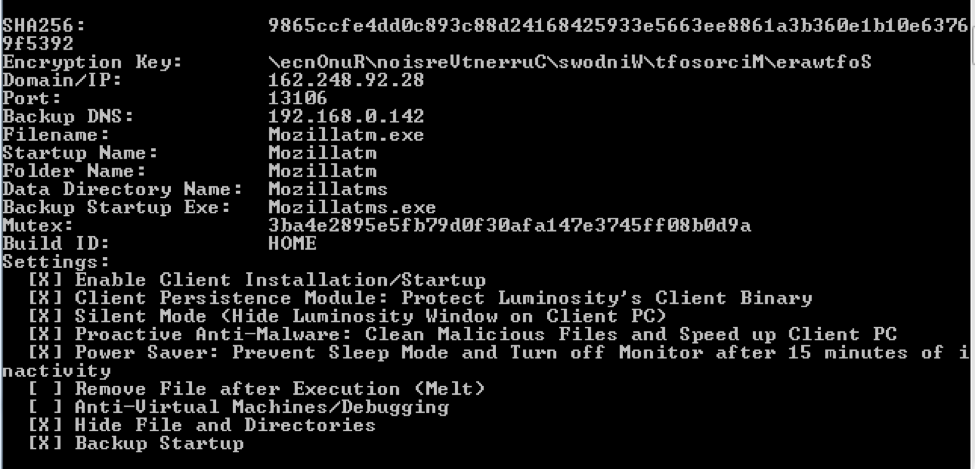
Later, it creates a windows startup item with the same binary in order to remain persistent. The item which was added to the windows startup was found to be named as mozillatm.exe. Other than this there is another backup startup option registered, named as mozillatms.exe.
Mozillatm.exe is a .net executable and the file is highly obfuscated.
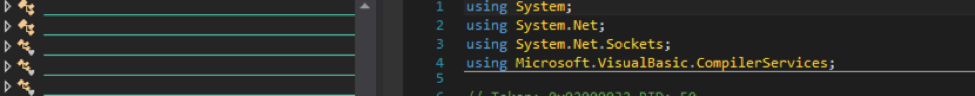
We identified a cryptography library inside the malware. This library is used to encrypt/decrypt C&C communication. It was observed that the malware loads the cryptographic library into memory.
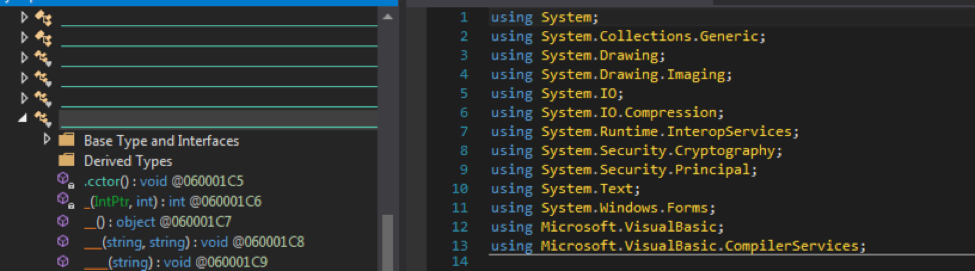
The malware is classified as an active persistent threat, even though it is not a proper FUD malware but it used an encryption method and went under the hood for many popular antivirus.
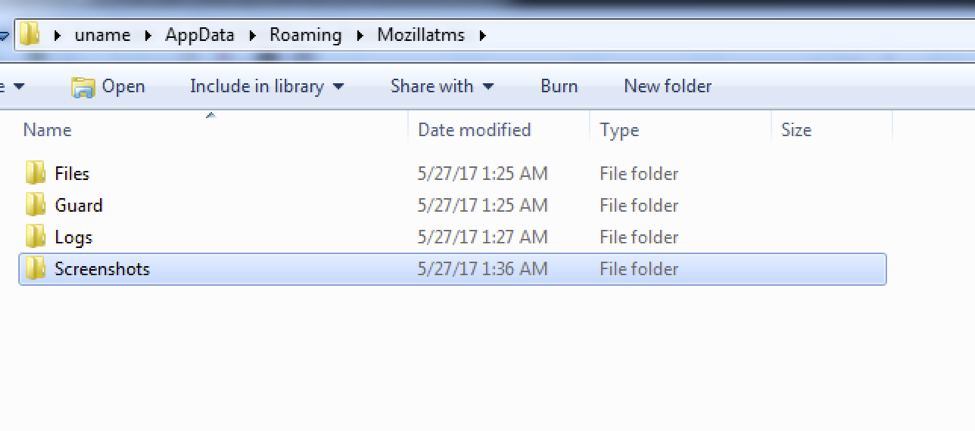
The malware creates a folder in the following location and stores victims key stroke logs, screenshots etc on different folder. We found evidence that these stolen screenshot and logs are transmitted to the c&c server time to time.
%USERPROFILE%\AppData\Roaming\Mozillatms
Command and Control(C2) Hunt
The malware connects to a command and control server via TCP protocol. The analysed sample connected to 162.248.92.2 on port 13106.
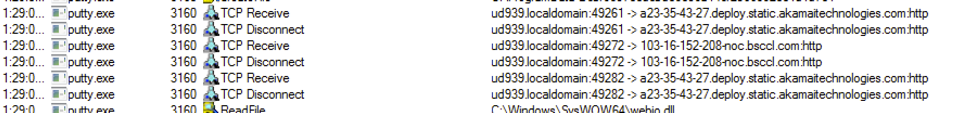
The malware transmits various information of the active window to the c2 server.
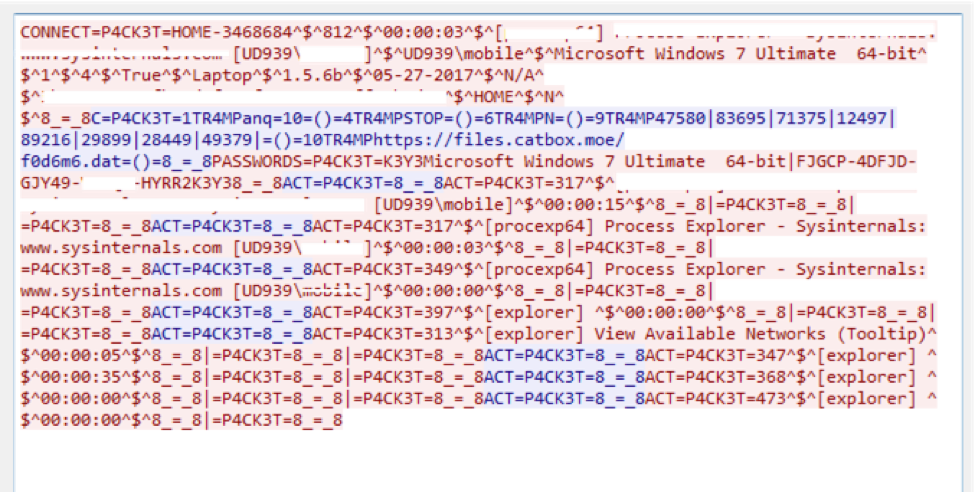
We got our hands on the malware configuration by analysing the behaviour and dissecting the malware with the help of readily available community tools.
Motivation
The purpose of this specific attack is not clear yet. The mother RAT, Luminosity has a feature of cryptocurrency mining via slave machines. That might be a reason given the current hype on cryptocurrency markets, but there was no solid evidence for this claim. However, the attacker group are well oriented about Bangladeshi peoples psychology which can be understood by analyzing their scamming pattern and offers like "bio-metric registered sim information fetching" or "free internet campaign" etc.
Damage
We could not determine the number of total infected users, but given the spreading mechanism and scamming offers, it is obvious that there are already thousands of victim affected by this attack.
To summarize: The affected PCs are now being remotely access and controlled by the actor or actors behind this attack. The attacker has been collecting logs on Keystrokes, accessing files and uploading them and in some cases may also have remote access of webcams and microphones.
For future reference, do not click on unknown links and do not download junk files. If it sounds too good to be true, it probably is. Be smart! Be safe!
Samples
SHA256: 25e6adab5bf30d2a47279a4a1de6f44700d422277b8dfdcc6cdd79cf96468692
File name: PC-NET-Setting.doc
SHA256: 979fb79fa18c507f7a46e1342a7efaf36558fa42859f903358c6e7429863b221
File name: PC-NET-Setting1.doc
SHA256: 47f9f2f332623dac8ce7b6468f83c0f9e9d87262dde5fd4d102321c7ab4263e8
File name: PC-NET-Setting2.doc
SHA256: 6f1fd6e920afe0594fef80888c8f78e0c1d990f45400623dfd13059c54634507
File name:
Owner-Information.doc
biometric-data-all-number.doc
SHA256: 9865ccfe4dd0c893c88d24168425933e5663ee8861a3b360e1b10e63769f5392
File name:
btcl.exe
download.exe
PC-NET.exe
bd2bd.exe
REVETM.exe
Registerbd.exe
ChromeTM.exe
BD2BD.exe
Mozillatm.exe
Conclusion
Our findings prove that there is a competent threat actor working behind this threat, now given that to collect such massive data takes an incredible amount of resources, time, manpower and motivation, we assess there could be a group actor involved.
During the course of our research, we did manage to identify a few individuals who we think are associated with this attack. We will not make their identities public here, but if any law enforcement agency asks us for it, we'd happily comply.
This is currently an ACTIVE THREAT FOR BANGLADESH!!