Intelligence-Driven incident response and hunting - enhances the speed and effectiveness of cyber threat detection.
Nowadays most organization have an OPSEC team, they strive to place an effective defense to detect and mitigate custom-crafted attacks and infiltration. Traditional threat detection tools and exploit inherent weaknesses in modern networks. Infiltration, does not need to result in data breach or other forms of business impact , if organizations learn and are adept at detecting and responding to attacks early. Many organizations respond and take action after the incident occurs.
If your organization still falls on this catagory, suggest you to read the following: reactive cyber security strategy is not a strategy.
Welcome back! Great, you’ve decided to move on to focusing on a proactive approach to Incident Response. Now, I remind you, most dangerous attackers aren’t part-time activists or moonlighters just looking in on your organization’s assets. They’re professionals looking to make money. They’re nation-states looking to advance their strategic agenda. They take advantage of 0days, application vulnerabilities, your unpatched devices, social engineering your people. To be able to solve this, the strategy needs to be adjusted. Intelligence Driven Security is now considered as a strategy for solving the most serious and sensitive security challenges today. Intelligence Driven Security stops cyber attacks before the damage is done.
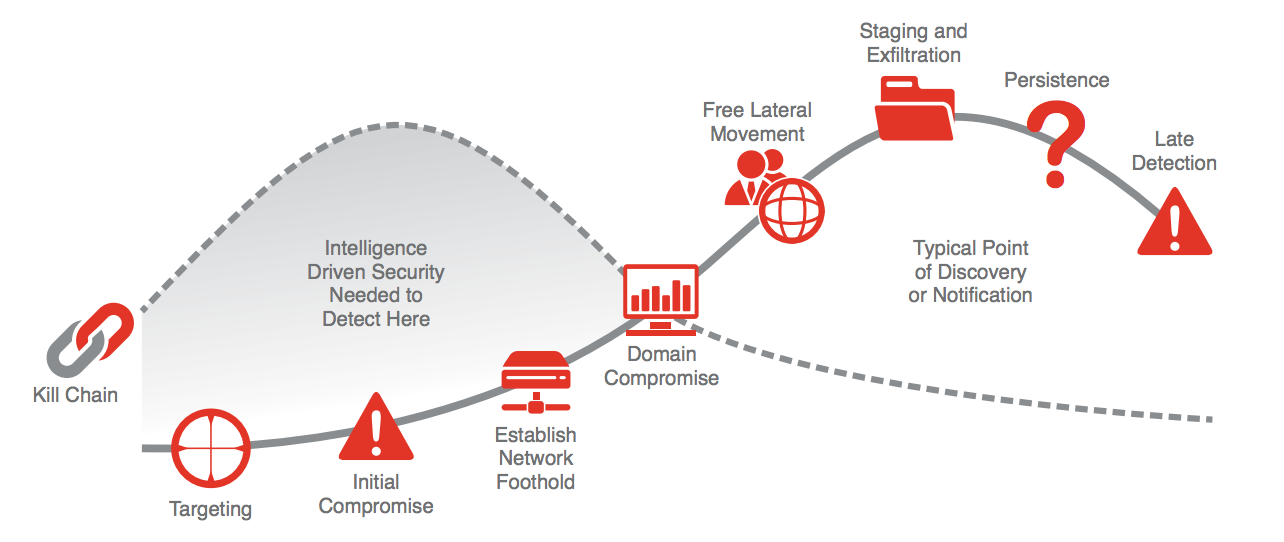
source: https://www.rsa.com/content/dam/rsa/PDF/h1304-intelligence-driven-threat-detection-response-wp.pdf
So, in order to apply the Intelligence Driven Security strategy to incident detection and response, you need to build a hunting team capable of doing:
- Network and endpoint monitoring
- Advanced analysis of security-related data
- Malware identification and analysis
- Incident response and breach remediation
Now, want to build a hunting team? This team needs to understand intelligence concepts in information security like F3EAD. Standing for Find, Fix, Finish, Exploit, Analyze, and Disseminate, this is a methodology for combining operations and the intelligence process.
The team needs to go beyond just capturing networks and endpoints logs. They need to be able to deploy wherever monitoring is needed. They need to do full network packet-capture means recording, parsing, normalizing, analyzing and reassembling all data traffic at every layer of the network stack. They need to analyze and tag to facilitate subsequent threat analysis and investigation. The obvious challenge is data collection and parsing in real-time.
At this point, advanced analytics are done to uncover hidden threats. A good hunting team can use a basic indicator, but the more options a team has for getting telemetry (data), the better their chances of identifying and corroborating malicious actions. The hunting team needs to scale the whole analysis with the help of modern data science. Many open source tools are available for scalability & automation. Check Incident Response Hunting Tools to know about a few tools in this era. The tools can help the team but the hunting is a mindset, an idea of focusing on proactive action, rather than reactive response. Here, man and machine work together to enhance the speed and effectiveness of cyber threat detection.
Intelligence Driven threat detection and response helps organizations achieve high standards of security. However, adding this type of an advanced and capable hunting team needs time and a decent budget. The kick start time is also high if your organization does not have this expertise from before. If you are planning to build a hunting team or want to improve your proactive response our team, the Beetles Team, can help you in many aspects.
Wait! If you reach here. Look like you love to read, don’t miss these