Grsecurity: Enhance your Linux server security. [Part 1]
As a member of the cybersecurity community as well as working as a security engineer, I need to deal with many attempted attacks on my servers. Specially, when a server comes with a vulnerable application, I need to fix them one by one. Most of the time, it is difficult to provide a good security solution when the kernel is vulnerable. So, I have no other way to update it with vanilla kernel and sometimes for a few applications, is depends on specific kernel version. Then, the only way that is left for me is patching.
Another scenario came to me, that if a non root user can login to system via SSH and their kernel could be vulnerable to privilege escalation exploits such as buffer overflows. So, I needed to implement Role Based Access Control (RBAC). Then GRSecurity came to rescue.
GRSecurity has a collection of security features for the Linux kernel, including address space protection, enhanced auditing and process control. It also has a component named PaX, which is not actually developed by GRSecurity developers but, provides address space layout randomization (ASLR), which randomizes important memory addresses to reduce the probability of attacks that rely on easily predicted memory addresses.
Long story short : Today, I am writing this article with a quick and dirty approach on GRSecurity patching. I think it will be helpful for beginners.
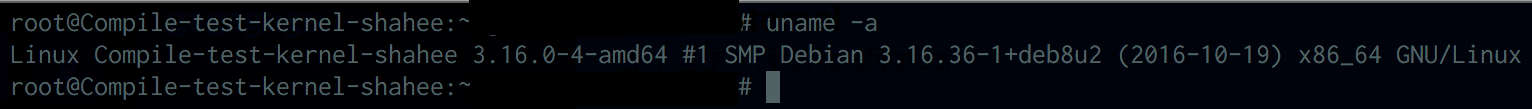
Well, here is my box information:
OS: Debian 8.6 (jessie) 64bit
CPU: 8 core
RAM: 16GB
Kernel: 3.16.X
Step1:
$ sudo apt-get update
$ sudo apt-get upgrade
Step2:
$ sudo apt-get install libncurses5-dev build-essential kernel-package git-core gcc-4.9 gcc-4.9-plugin-dev make
Step3:
$ mkdir grsec
$ cd grsec/
$ wget https://grsecurity.net/spender-gpg-key.asc
$ gpg --import spender-gpg-key.asc
$ gpg --recv-key 6092693E
Step4:
$ wget https://www.kernel.org/pub/linux/kernel/v3.x/linux-3.18.1.tar.xz
$ wget https://www.kernel.org/pub/linux/kernel/v3.x/linux-3.18.1.tar.sign
$ unxz linux-3.18.1.tar.xz
$ gpg --verify linux-3.18.1.tar.sign
if failed, do this step again.
Step5:
$ wget http://deb.digdeo.fr/grsecurity-archives/kernel-3.18/grsecurity-3.0-3.18.1-201501042021.patch
$ wget http://deb.digdeo.fr/grsecurity-archives/kernel-3.18/grsecurity-3.0-3.18.1-201501042021.patch.sig
$ gpg --verify grsecurity-3.0-3.18.1-201501042021.patch.sig
Step6:
$ tar -xf linux-3.18.1.tar
$ cd linux-3.18.1/
$ patch -p1 < ../grsecurity-3.0-3.18.1-201501042021.patch
Step 7:
$ cp /boot/config-$(uname -r) .config
$ make menuconfig
Navigate to Security options
Navigate to Grsecurity
Press Y to include it
Set Configuration Method to Automatic
Set Usage Type to Server (default)
Set Virtualization Type to None (default)
Set Required Priorities to Security
Select Exit
Select Exit
Select Exit
Select Yes to save
Step8:
$ make-kpkg clean
$ export CONCURRENCY_LEVEL="$(grep -c '^processor' /proc/cpuinfo)"
(if this command return 4 then --jobs=4 , if return 1 or 2 then --jobs=1 or --jobs=2)
$ sudo make-kpkg --jobs=8 --initrd kernel_image
[it took 2 to 4.5 hour]
Step9:
$ cd ..
Step10:
$ sudo dpkg -i *.deb
$ sudo update-grub
if you are getting this warning like:
Warning: Setting GRUB_TIMEOUT to a non-zero value when GRUB_HIDDEN_TIMEOUT is set is no longer supported.
Then,
$ sudo nano /etc/default/grub
Change:
GRUB_HIDDEN_TIMEOUT=0
to
#GRUB_HIDDEN_TIMEOUT=0
then,
$ sudo update-grub
$ sudo reboot
Done:
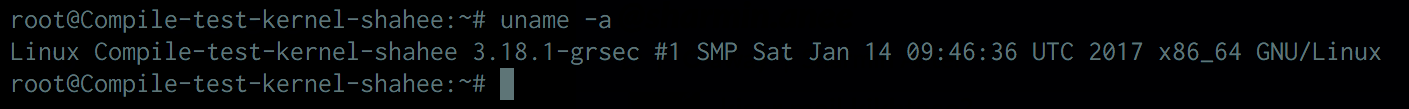
I will continue my writing on grsecurity to advanced implementations.