Unveiling the Hidden: The Chatroom Message Retrieval Vulnerability - A Deep Dive into User Privacy and Data Security
Introduction
In the realm of security testing, a recent endeavor led to a startling discovery within an open-source modern forum software platform. This platform, renowned for its fusion of contemporary mobile and social web communication tools with the deep-rooted community engagement of traditional Internet bulletin boards, is known as NodeBB. Offering a mobile-responsive design and an extensible platform built on Node.js, NodeBB is lauded for its real-time forum software capabilities, extensibility through plugins, responsive design, and robust user management. However, this deep dive into its features unearthed a critical vulnerability within its chatroom function, one that has far-reaching implications for user privacy and data security.
Platform Overview
The open-source modern forum software solution in question is a versatile platform that harmonizes contemporary communication tools from the mobile and social web with the enduring community engagement characteristic of classic Internet bulletin boards. It features a mobile-ready design and an extensible platform built on Node.js, offering a range of features, including real-time forum software, responsive design, extensibility through plugins, and robust user management. One of its standout features is the chatroom function that allows users to create chat rooms, add or remove participants, and engage in real-time conversations, offering a comprehensive user experience.
Vulnerability Discovery
The Enigma of Message Deletion
Our investigation commenced with an in-depth exploration of the platform's chatroom capabilities. In our initial attempts, we scrutinized the chatbox for Cross-Site Scripting (XSS) vulnerabilities, but these efforts yielded no results. Intriguingly, our focus then shifted towards investigating other facets of chatroom functionality, specifically the process of message deletion.
It was during this phase that an intriguing phenomenon within the platform's chatroom came to light. Users had the ability to delete their messages through an API endpoint, facilitated via a DELETE request. The enigma lay in the fact that these deleted messages were not channeled through any API request, raising questions about the mechanics governing their removal.
During our extensive examination of the chatroom feature of the open-source forum software, we encountered a puzzling aspect related to the message deletion process. Users had the capability to remove their messages, a feature facilitated by an API endpoint that employed the DELETE request method. What was particularly intriguing about this discovery was the conspicuous absence of any visible API request associated with the messages that were being deleted. This anomaly led us to question the underlying mechanics governing this unusual deletion process.
The Role of the DELETE Request
1#. When a user chose to delete one of their messages, the platform initiated a DELETE request to a specific API endpoint, as exemplified here:
DELETE /api/v3/chats/1/messages/3 HTTP/2
Host: beetles.io
...
2#. This DELETE request served as the trigger for the removal of the specified message, and the server would respond accordingly. A successful deletion invoked a response similar to the following:
{"status":{"code":"ok","message":"OK"},"response":{}}
3#. Conversely, if the deletion attempt was unsuccessful due to the message having already been deleted, the response conveyed a message such as:
{"status":{"code":"bad-request","message":"This chat message has already been deleted."},"response":{}}
The Enigma: Missing API Request
However, what struck us as odd was the absence of any observable API request connected to the messages being deleted. When users interacted with the chatroom, their messages seemingly vanished upon deletion without any apparent trace of the usual API involvement one would expect. This deviation from the norm raised several questions and piqued our curiosity.
We pondered how the platform managed the deletion process without a visible API request. Typically, when a message is deleted, the expectation is that a specific API call triggers its removal, and the server responds accordingly. In this case, the conspicuous absence of a visible API request led to a deeper examination of the platform's mechanics.
The discrepancy in the deletion process was the initial clue that something unconventional was occurring within the chatroom's message management. Our analysis pointed towards messages being managed in an unconventional manner, hinting at an underlying mechanism that differed from traditional methods employed in similar platforms.
This discovery opened the door to a deeper investigation, eventually revealing that every message sent within the chatroom was stored with unique IDs and could be accessed through an API endpoint, a revelation that was instrumental in our subsequent exploration of the message retrieval vulnerability.
The Revelation of Message Retrieval
In essence, every message sent within the chatroom was tagged with a unique identifier, effectively anchoring them within the platform's infrastructure. Each message, regardless of its content or origin, was assigned a specific identification code. This practice stood in contrast to conventional messaging systems where messages might be subject to deletion, and once removed, they would typically be considered irretrievable.
The platform's decision to employ unique IDs for message tracking was a pivotal point in our investigation. This mechanism allowed the software to maintain a record of each message's existence, even after its apparent deletion. The implication was clear: the platform held a repository of messages, each marked by its individual identifier, rather than entirely removing them from the system upon deletion.
This practice contradicted the standard expectation that deleted messages would be permanently eradicated, with no avenue for retrieval. Instead, it suggested that the platform had an unconventional method for handling messages, one that deviated from the conventional approach employed by mainstream chat platforms.
Attempted Deletion and "401 Unauthorized" Response
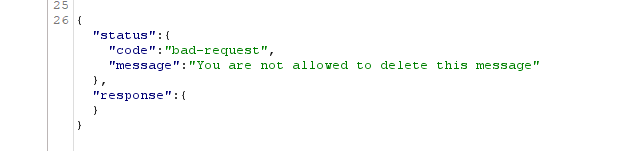
Our understanding of this unique message management system deepened as we attempted to delete messages sent by other users. To our surprise, these attempts were met with an unyielding "401 unauthorized" response from the platform. This response, while initially perplexing, was a crucial clue in our investigation.
The "401 unauthorized" response signified a restriction placed upon users attempting to delete messages sent by others. It was a clear indication that the platform had implemented access controls and limitations to prevent users from tampering with messages belonging to different individuals.
Exploiting the Vulnerability
Concealing, Not Erasing
Traditionally, when a user deletes a message in a chat platform, the expectation is that the message is permanently eradicated, with no means for retrieval. However, what we found on this platform was a stark departure from this conventional behavior. The platform's unique approach involved concealing deleted messages while retaining them in the system's infrastructure. These messages were essentially marked as hidden from regular view, but they still existed within the platform, marked with their unique identification codes.
This divergence in behavior, where deletion was synonymous with concealment rather than obliteration, was the fundamental aspect that allowed us to exploit the vulnerability.
Modifying the DELETE Request
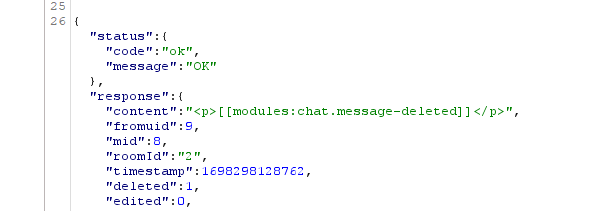
The pivotal moment came when we realized that, due to this concealment, we could potentially retrieve the deleted messages. The platform's approach implied that these messages were not entirely gone, and their retrieval might be possible. This realization prompted us to experiment and exploit the vulnerability further.
Our ingenious modification involved switching the DELETE request, which was intended for message deletion, to a GET request. This maneuver was executed using a repeater tool, which allowed us to manipulate the request method from DELETE to GET.
A GET request is typically employed to retrieve data from a server, and by employing this request method, we were essentially asking the platform to provide us with the contents of the supposedly deleted messages, rather than deleting them. The platform, due to its peculiar message management system, complied with our request, returning the contents of the deleted messages.
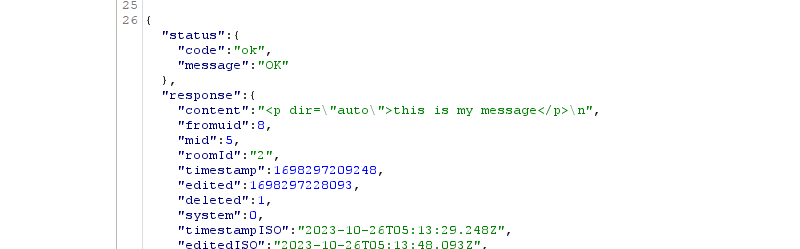
Replicating the Method
To further solidify our findings and demonstrate the gravity of the vulnerability, we replicated this method from another user's account. The results were identical. This meant that any user, with minimal technical expertise and access to a repeater tool or a similar mechanism, had the capability to retrieve the deleted messages of any other user within the chatroom.
The impact of this vulnerability became crystal clear - it posed a significant threat to user privacy and data security, allowing for unauthorized access to sensitive information exchanged within the platform.
Impact Assessment
Message Privacy and History Exposure
The discovery of the message retrieval vulnerability had far-reaching implications, particularly in the context of user privacy and data security within the chat platform. The ramifications of this vulnerability extended deep into these critical areas, essentially turning the standard expectations of a chat platform on their head.
The Standard Expectation
In virtually every chat platform, there is an unspoken understanding and expectation regarding message privacy and history. Users anticipate that they will not be able to access or retrieve messages exchanged within a group chat that occurred before their entry. This expectation is rooted in a fundamental principle of user privacy and data security. It provides a sense of confidentiality and control over one's digital conversations.
The Breach of User Privacy
However, the message retrieval vulnerability shattered this conventional understanding. It allowed any user, with the means to exploit the vulnerability, to access messages that were, by all accounts, deleted. In essence, this capability represented a substantial breach of user privacy. It violated the user's trust in the platform's ability to manage their data securely and in accordance with standard privacy expectations.
When a user believes they have deleted a message, it's a reasonable expectation that the message is irretrievably gone from the platform's servers. The discovery that these deleted messages were not only retained but also accessible was a direct affront to user privacy.
Exposure of Sensitive Information
The potential exposure of sensitive information added another layer of concern. Chat platforms are often used for a wide range of conversations, from personal and intimate discussions to professional and confidential exchanges. Users depend on the platform to maintain the privacy of these conversations. However, the vulnerability put these sensitive conversations at risk of unauthorized access.
Imagine a scenario in which users had shared confidential business information, personal details, or sensitive discussions within the chatroom. The existence of the vulnerability meant that these discussions were not as private as users had assumed. The potential for unauthorized access to this information was a stark reminder of the importance of robust data security in chat platforms.
The Implications for Data Security
Beyond just user privacy, the vulnerability also had significant implications for data security. Chat platforms are not only repositories of conversations but can also contain files, images, and other data shared among users. The ability to access deleted messages indicated a breakdown in data security, as sensitive files and information might also be at risk.
Conclusion
Our comprehensive penetration testing of this open-source forum software exposed a critical vulnerability within its chatroom functionality. This vulnerability enabled the retrieval of deleted messages, and its impact on user privacy and data security was profound. Our responsible disclosure of this issue prompted the platform's development team to address it promptly, mitigating potential privacy breaches.
This experience underscores the vital importance of responsible disclosure and underscores the ongoing need for security assessments in modern software applications. As security professionals, it is our duty to identify and address vulnerabilities, safeguard the integrity of digital platforms, and protect the trust and privacy of their users. This vulnerability serves as a testament to the critical role we play in upholding the security of digital systems and safeguarding user data.
And this is what after the fix!